Wednesday, March 31, 2021
SPACE - S0 - 20210331 - 12K and 100K Cycles Resetting, Spraying the Sky
Tuesday, March 30, 2021
3 Russian nuclear submarines simultaneously punch through Arctic ice
A video released by Russia's Ministry of Defence shows the conning towers of the three subs breaking through a continuous sheet of floating ice near the Franz Josef Land archipelago, in the Arctic Ocean north of the Barents Sea.
The subs are taking part in Umka-2021 (meaning "polar bear" in the Siberian Chukchi language) — an expedition to the region that involves 600 military and civilian personnel, including staff from the Russian Geographical Society, a non-governmental organization established in the 19th century.
The three submarines broke through 5-foot-thick (1.5 meters) ice to surface within 1,000 feet (300 m) of each other at the same time, "for the first time in the history of the Navy," Russian navy commander Admiral Nikolay Yevmenov told Russia's President Vladimir Putin in a televised video call.
The conditions in the region were between minus 13 and minus 22 degrees Fahrenheit (minus 25 and minus 30 degrees Celsius), with winds gusting at up to 70 mph (110 km/h), the admiral reported.
Surface submarines
Surfacing a submarine through thick sea ice is no easy feat. According to a 2018 article in Popular Mechanics about American submarines in the Arctic, bursting through the ice requires careful preparation.
Nuclear-powered missile submarines usually try to stay hidden beneath Arctic ice because it makes them effectively invisible to enemies. But when they do have to come to the surface, a sub commander will first try to find nearby patches of open water — such as a "lead" or "polynya" — where they can surface without encountering any floating ice.
When that fails, careful maneuvering is needed so that the submarine can break through up to 9 feet (2.5 m) of sea ice.
The first task is to slowly raise the submarine until its upper tower makes contact with the bottom of the floating ice layer. Compressed air is then used to push seawater out of the submarine's ballast tanks, creating an upward force, until that force cracks the ice.
Getting three submarines to break through the ice at the same time is especially difficult, because the underwater vessels can't communicate with each other.
Arctic expedition
Although this is the first time Russian submarines have surfaced through the ice together, it may not be the first time it has been done.
Popular Mechanics reported that two U.S. submarines — the USS Connecticut and the USS Hartford — surfaced through the Arctic ice within sight of the British submarine HMS Trenchant in 2018.
Russia's military didn't name the three vessels that took part in the latest operation, but the Barents Observer news site identified them as two Delta-IV nuclear-powered ballistic missile submarines — the mainstay of the Soviet submarine fleet during the Cold War — and a newer Borei-class sub; the class names comes from Boreas, the Greek god of the north wind.
Each Russian submarine is thought to carry up to 16 ballistic missiles, and each missile can carry up to six individual nuclear warheads.
The Umka-2021 expedition near Russia's Franz Josef Land archipelago began on March 20 under the command of the Russian navy.
"For the first time, according to a single concept and plan, a complex of combat training, scientific research and practical measures of various directions is being carried out in the circumpolar regions," Yevmenov told Putin in the video call.
A key result was that the "technical characteristics" of various weapon systems, military equipment and special equipment had been confirmed in conditions of high latitude and low temperatures, he said.
Russia has proposed that the Arctic could become a major route for commercial shipping, which could be shepherded through the sea ice by nuclear-powered "icebreaker" ships.
Originally published on Live Science.
SPACE - S0 - 20210330 - New Aurora, Ancients Knew Astronomy, Baby Star Jets
SPACE - S0 - 20210330 - New Aurora, Ancients Knew Astronomy, Baby Star Jets
Good Morning, 0bservers!
Monday, March 29, 2021
BluMetric Environmental Keeping the CAF Awash in Fresh, Clean Water
“BluMetric is a company that's really all about integrated solutions,” said company CEO Scott MacFabe. “We have a very strong consulting history and we have a strong technology history and the two complement each other very, well.”
“We have provided solutions, services and support to the Canadian Armed Forces for many years – with a particularly strong presence within the Royal Canadian Navy (RCN) – and are truly becoming the water subject matter experts for the Canadian defence industry,” he added. “As well, our experts are on-call 24-7 to support our water treatment and are ready to deploy in any situations -- including combat zones.”
AT SEA
The clearest proof of BluMetric’s stature with the Canadian Armed Forces is the number of supply/support contracts it has with DND.
A case in point: BluMetric currently has an $18.4 million contract (signed July 2018) to support the SRODs installed on the RCN’s Halifax class frigates.
As the name suggests, Shipboard Reverse Osmosis Desalinators provide naval ships with fresh, pure drinking water extracted from the oceans that the ships are sailing in. In the case of the RCN’s Halifax class frigates, BluMetric is overhauling/updating their existing SRODs (previously supplied/installed by the company) to bring them up to the most modern standards.
The goal of this contract is to significantly modify the frigates’ SRODs, so that they can be operated with minimal maintenance/supplies during a typical 90-day deployment at sea. Making this happen entails reducing the amount of ‘consumables’ needed to filter and purify salt water.
“We want the ships to be able to produce potable water using far less energy and far fewer consumables for a longer period of time, which helps in their 90- day deployments and supports the green fleet initiative,” said Corey Switzer, BluMetric’s Military Market Leader and PMO Manager. “Reducing the environmental footprint of generating this fresh water is critical for the fleet, as is reducing the amount of scheduled maintenance which results in minimal downtime.”
The JSS project is also installing BluMetric’s new SUVUs (Shipboard Ultraviolet Units, contract signed/ March 2019) and SCDUs (Shipboard Chlorine Dosing Unit, contract signed/ March 2019) in its ships. Designed to work with the SROD, the SUVU allows a ship to safely treat any port-supplied fresh water using bacteria-killing UV light. Meanwhile, the SCDU monitors and doses chlorine levels in all ship-based water, be it from the SROD or the port. Think of it as a ‘Goldilocks device’. The SCDU ensures that the ship’s fresh water is neither over- nor under-chlorinated – it’s ‘just right’.
In addition to these DND naval contracts, BluMetric has signed a Standing Offer Agreement (May 2018) with SNC Lavalin to provide in-service support to the RCN’s Kingston class coastal defence vessels. It also has a Standing Offer Agreement with Federal Fleet Services Inc. (April 2018) to provide in-service support on the MV Asterix, the civilian ship that Federal Fleets substantially modified to supply our Navy at sea.
Most recently, BluMetric is pursuing a contract with the RCN to provide Oily Water Separators (OWS) for the Halifax class frigates. The OWS safely removes oil and other contaminants from a ship’s bilge water, which can accumulate where sea water interacts with the ship’s machinery. BluMetric and one other competitor are currently having their OWS tested by the RCN.
ON LAND
In 2017, BluMetric signed a contract with DND to support the Canadian Army’s ROWPUs (Reverse Osmosis Water Purification Systems). Under the deal, the company is being paid $3.5 million to support the ROWPUs, and $1.8 million to provide the land forces’ ROWPUs with 90 Day Sustainment Kits. These water purification units are used for military operations and disaster relief deployments anywhere Canada’s help is needed in the world.
As with its SRODs, BluMetric has been working diligently to reduce the energy and consumables needed to operate its ROWPUs. “What we've done is revolutionized the pre-filtration unit so that everything is automatically back-washed,” said Switzer. “This allows the system to run 90 days without requiring filter changes, which reduces downtime, the money spent on consumables, and the huge amount of waste generated by using disposable filters.” BluMetric’s ROWPUs are also designed to filter out CBRN (Chemical, Biological, Radiological and Nuclear) contaminants from the water, which can be truly life-saving in conflict zones.
END-TO-END SERVICE
BluMetric’s success in winning numerous DND contracts speaks to the company’s commitment to building quality water treatment systems that are easy to operate, generate consistently clean water, and function as designed for years at a time.
This said, the real secret to BluMetric’s success is its end-to-end service. “We don't consider the job done when the tech has been shipped out,” said MacFabe. “We work very closely with our clients to make sure that integration and deployment are seamless, and that they have the necessary training and support to be able to run it themselves. And when problems that they can’t fix come up – and they inevitably do because it's technology that we’re talking about – we're right there to support them and to make sure that their downtime is as short as possible.”
“BluMetric’s commitment to service has stood up even during the pandemic,” Switzer added. “Right now, we have field service representatives travelling to the East Coast, West Coast, and Northern Canada to support our clients and resolve their problems.”
MacFabe added, “it's hard for me to hide my pride in this aspect of our business and how the team, led by Corey, has been there for our clients throughout COVID-19.”
Add BluMetric’s belief in paying attention to customer feedback – “the more we listen, the better we make the technology,” said MacFabe – and one can see why this Ottawa company is doing so well in the Canadian defence sector. After all, water is life for everyone who serves in the CAF (as well as everyone else on the planet). By doing its best to keep the CAF supplied with potable water, BluMetric has proven itself to be an essential partner for DND and the men and women who serve in the CAF.
Sunday, March 28, 2021
Huge uptick in lightning over the Arctic in past decade, research shows
https://phys.org/news/2021-03-huge-uptick-lightning-arctic-decade.html
A combined team of researchers from the University of Washington and the University of Otago has found that lightning strikes in the Arctic have been rising dramatically over the past decade. In their paper published in the journal Geophysical Research Letters, the group describes their study of data from the World Wide Lightning Location Network (WWLLN) and what they found.
Lightning is much less common in colder parts of the planet—the chill is less conducive to the humidity required for electrically charging ice crystals in clouds. In this new effort, the researchers found that for one cold region, the number of lightning strikes has been increasing dramatically as average air temperatures rise due to global warming. Notably, prior research has shown that temperatures are rising approximately three times faster in the Arctic than in the rest of the world.
The work began as team members in Washington began noticing more lightning strikes in Arctic regions—they were studying data from the WWWLLN, which is run by the University of Washington. That led to a more in-depth study, one focused on comparing the number of lightning strikes in northern parts of Canada, Siberia, Alaska and the Arctic Ocean—basically, anything above 65 degrees latitude. They focused their efforts on summing the number of strikes in the Arctic region for the years 2010 to 2020.
Data, mainly for the summer months, showed the average number of lightning strikes in a given year for the entire region rose from approximately 18,000 to over 150,000. Worried that the massive increase might be due to improvements in technology, the researchers adjusted for sensor differences and compared what they found with lightning strikes in other parts of the world over the same time period. The results remained the same. But the comparison showed that lightning strikes in the Arctic, once accounting for 0.2% of all lightning strikes across the planet in 2010, accounted for 0.6% in 2020.
The researchers suggest that in addition to providing a reminder of the warming of the planet, their findings will likely influence land managers in the Arctic to step up their approach to handling forest fires that result from the increase in lightning strikes.
Saturday, March 27, 2021
Defense News: IAI completes live-fire tests of 150km-range Barak air defense system
IAI completes live-fire tests of 150km-range Barak air defense system

Photo: IAI
Israel Aerospace Industries (IAI) on Monday completed a series of successful live-fire tests of the Barak air defense system. The tests were carried out to evaluate the system’s capability to deal with a range of scenarios and threats, including the interception of a ballistic target by the Barak ER (extended range) interceptor.
The Barak ER missile, part of the Barak family of interceptors developed by IAI, is capable of intercepting ballistic and non-ballistic threats at a range of 150 kilometers. The extended range is made possible in part by adjusting the interceptor and the missile system's MMR radar to a 150 km range, according to the company.
The vertically-launched missile includes a booster, a dual-pulse rocket motor, and an advanced radar homing seeker.
Israeli has completed direct fire trials with BARAK Air Defense System, Mar 23, 2021
Boaz Levy, IAI president and CEO, said "The evolution of airborne threats across the globe, combined with geopolitical changes, requires an advanced, agile, and versatile air defense system. The Barak system was operationally proven against countless threats, including some of the most challenging ones today.
The trial series we completed today enhances the proven capabilities against wider range of threats. The successful trial further demonstrates the robustness of the Barak system's based on IAI's innovation, technological capabilities and decades of experience in developing air defense systems. The combination of several interceptors in a unified launcher and the inherent modularity of the Barak system provide an optimal response for the future battlefield, offering the forces unprecedented operational agility and flexibility.”
SPACE - S0 - 20210327 - Apophis, Scary Solar Forecast, Galactic Burst
SPACE - S0 - 20210327 - Apophis, Scary Solar Forecast, Galactic Burst
Good Morning, 0bservers!
Google’s top security teams unilaterally shut down a counterterrorism operation
Google’s security teams publicly exposed a nine-month hacking operation
What wasn’t disclosed: The move shut down an active counter-terrorist operation being conducted by a Western government
The decision has raised alarms inside Google and elsewhere
Google runs some of the most venerated cybersecurity operations on the planet: its Project Zero team, for example, finds powerful undiscovered security vulnerabilities, while its Threat Analysis Group directly counters hacking backed by governments, including North Korea, China, and Russia. And those two teams caught an unexpectedly big fish recently: an “expert” hacking group exploiting 11 powerful vulnerabilities to compromise devices running iOS, Android, and Windows.
But MIT Technology Review has learned that the hackers in question were actually Western government operatives actively conducting a counterterrorism operation. The company’s decision to stop and publicize the attack caused internal division at Google and raised questions inside the intelligence communities of the United States and its allies.
Attackers are exploiting the same types of software vulnerabilities over and over again, because companies often miss the forest for the trees.
A pair of recent Google blog posts detail the collection of zero-day vulnerabilities that it discovered hackers using over the course of nine months. The exploits, which went back to early 2020 and used never-before-seen techniques, were “watering hole” attacks that used infected websites to deliver malware to visitors. They caught the attention of cybersecurity experts thanks to their scale, sophistication, and speed.
Google’s announcement glaringly omitted key details, however, including who was responsible for the hacking and who was being targeted, as well as important technical information on the malware or the domains used in the operation. At least some of that information would typically be made public in some way, leading one security expert to criticize the report as a “dark hole.”
“Different ethical questions”
Security companies regularly shut down exploits that are being used by friendly governments, but such actions are rarely made public. In response to this incident, some Google employees have argued that counterterrorism missions ought to be out of bounds of public disclosure; others believe the company was entirely within its rights, and that the announcement serves to protect users and make the internet more secure.
“Project Zero is dedicated to finding and patching 0-day vulnerabilities, and posting technical research designed to advance the understanding of novel security vulnerabilities and exploitation techniques across the research community,” a Google spokesperson said in a statement. “We believe sharing this research leads to better defensive strategies and increases security for everyone. We don’t perform attribution as part of this research.”
It’s true that Project Zero does not formally attribute hacking to specific groups. But the Threat Analysis Group, which also worked on the project, does perform attribution. Google omitted many more details than just the name of the government behind the hacks, and through that information, the teams knew internally who the hacker and targets were. It is not clear whether Google gave advance notice to government officials that they would be publicizing and shutting down the method of attack.
But Western operations are recognizable, according to one former senior US intelligence official.
“There are certain hallmarks in Western operations that are not present in other entities … you can see it translate down into the code,” said the former official, who is not authorized to comment on operations and spoke on condition of anonymity. “And this is where I think one of the key ethical dimensions comes in. How one treats intelligence activity or law enforcement activity driven under democratic oversight within a lawfully elected representative government is very different from that of an authoritarian regime.”
“There are certain hallmarks in Western operations that are not present in other entities … you can see it translate down into the code.”
“The oversight is baked into Western operations at the technical, tradecraft, and procedure level,” they added.
Google found the hacking group exploiting 11 zero-day vulnerabilities in just nine months, a high number of exploits over a short period. Software that was attacked included the Safari browser on iPhones but also many Google products, including the Chrome browser on Android phones and Windows computers.
But the conclusion within Google was that who was hacking and why is never as important as the security flaws themselves. Earlier this year, Project Zero’s Maddie Stone argued that it is too easy for hackers to find and use powerful zero-day vulnerabilities and that her team faces an uphill battle detecting their use.
Instead of focusing on who was behind and targeted by a specific operation, Google decided to take broader action for everyone. The justification was that even if a Western government was the one exploiting those vulnerabilities today, it will eventually be used by others, and so the right choice is always to fix the flaw today.
“It’s not their job to figure out”
This is far from the first time a Western cybersecurity team has caught hackers from allied countries. Some companies, however, have a quiet policy of not publicly exposing such hacking operations if both the security team and the hackers are considered friendly—for example, if they are members of the “Five Eyes” intelligence alliance, which is made up of the United States, the United Kingdom, Canada, Australia, and New Zealand. Several members of Google’s security teams are veterans of Western intelligence agencies, and some have conducted hacking campaigns for these governments.
In some cases, security companies will clean up so-called “friendly” malware but avoid going public with it.
“They typically don’t attribute US-based operations,” says Sasha Romanosky, a former Pentagon official who published recent research into private-sector cybersecurity investigations. “They told us they specifically step away. It’s not their job to figure out; they politely move aside. That’s not unexpected.”
While the Google situation is in some ways unusual, there have been somewhat similar cases in the past. The Russian cybersecurity firm Kaspersky came under fire in 2018 when it exposed an American-led counterterrorism cyber operation against ISIS and Al Qaeda members in the Middle East. Kaspersky, like Google, did not explicitly attribute the threat but nevertheless exposed it and rendered it useless, American officials said, which caused the operatives to lose access to a valuable surveillance program and even put the lives of soldiers on the ground at risk.
Kaspersky was already under heavy criticism for its relationship with the Russian government at the time, and the company was ultimately banned from US government systems. It has always denied having any special relationship with the Kremlin.
Google has found itself in similar water before, too. In 2019, the company released research on what may have been an American hacking group, although specific attribution was never made. But that research was about a historical operation. Google’s recent announcements, however, put the spotlight on what had been a live cyber-espionage operation.
Who’s being protected?
The alarms raised both inside government and at Google show the company is in a difficult position.
Google security teams have a responsibility to the company’s customers, and it is widely expected that they will do their utmost to protect the products—and therefore users—who are under attack. In this incident, it’s notable that the techniques used affected not just Google products like Chrome and Android, but also iPhones.
While different teams draw their own lines, Project Zero has made its name by tackling critical vulnerabilities all over the internet, not just those found in Google’s products.
The secretive security agency identified the vulnerability and is taking public credit as part of an effort to “build trust.”
“Each step we take towards making 0-day hard, makes all of us safer,” tweeted Maddie Stone, one of the most highly respected members of the security team, when the latest research was published.
But while protecting customers from attack is important, some argue that counterterrorism operations are different, with potentially life-and-death consequences that go beyond day-to-day internet security.
When state-backed hackers in Western nations find cybersecurity flaws, there are established methods for working out the potential costs and benefits of disclosing the security gap to the company that is affected. In the United States it’s called the “vulnerabilities equities process.” Critics worry that US intelligence hoards large numbers of exploits, but the American system is more formal, transparent, and expansive than what’s done in almost every other country on earth, including Western allies. The process is meant to allow government officials to balance the advantages of keeping flaws secret in order to use them for intelligence purposes with the wider benefits of telling a tech company about a weakness in order to have it fixed.
“The level of oversight even in Western democracies about what their national security agencies are actually doing is, in many cases, a lot less than we have in the United States.”
Last year the NSA made the unusual move to take credit for revealing an old flaw in Microsoft Windows. That kind of report from government to industry is normally kept anonymous and often secret.
But even though the American intelligence system’s disclosure process can be opaque, similar processes in other Western nations are often smaller, more secretive, or simply informal and therefore easy to bypass.
“The level of oversight even in Western democracies about what their national security agencies are actually doing is, in many cases, a lot less than we have in the United States,” says Michael Daniel, who was White House cybersecurity coordinator for the Obama administration.
“The degree of parliamentary oversight is much less. These countries do not have the robust inter-agency processes the US has. I’m not normally one to brag about the US—we’ve got a lot of problems—but this is one area where we have robust processes that other Western democracies just don’t.”
The fact that the hacking group hit by the Google investigation possessed and used so many zero-day vulnerabilities so rapidly could indicate a problematic imbalance. But some observers worry about live counterterrorism cyberoperations being shut down at potentially decisive moments without the ability to quickly start up again.
“US allies don’t all have the ability to regenerate entire operations as quickly as some other players,” the former senior US intelligence official said. Worries about suddenly losing access to an exploit capability or being spotted by a target are particularly high for counterterrorism missions, especially during “periods of incredible exposure” when a lot of exploitation is taking place, the official explained. Google’s ability to shut down such an operation is likely to be the source of more conflict.
“This is still something that hasn’t been well addressed,” the official said. “The idea that someone like Google can destroy that much capability that quickly is slowly dawning on folks.”
Friday, March 26, 2021
LiDAR acquires ranging signals with micron accuracy
Light Detection And Ranging (LiDAR) has been well known as it offers high ranging accuracy, and shows promising prospects in autonomous vehicles and various field. Traditional frequency modulated continuous wave (FMCW) LiDAR ranging is based on heterodyne detection, calculating unknown distance by extracting the frequency of the interference signal. However, such technique suffers from frequency modulation (FM) nonlinearity, which leads to inaccurate ranging results.
Due to the nonlinear relationship between the laser wavelength and injection current, the spectrum of the beat signal is broadened although the laser emits a triangle signal.
To solve the problem, a research team led by Prof. Zhang Wenfu from the Xi'an Institute of Optics and Precision Mechanics (XIOPM) of the Chinese Academy of Sciences (CAS) proposed a new approach that samples the ranging signals at equal frequency intervals using microresonator soliton comb. The results were published in Optics Letters.
In the new system, accurate beat frequency is not required so that the data processing step is significantly simplified. Instead, the unknown distance is given by the linear relationship between the measured frequency interval and the corresponding phase of the ranging signal.
Furthermore, thanks to the stable frequency characteristics of the soliton comb ensure accurate sampling, the system is almost impervious to external interference. The optical path of the system is almost unaffected by ambient temperature and humidity since the long optical fiber is not been used.
The experiment shows the ranging error is less than 20 μm at a measuring distance of 2 meters, the promising result and the advantages described above indicate the proposed approach has a strong application potential in precision manufacturing.
SPACE - S0 - 20210326 - Electric Earth Rotation Glitches Confirmed, Everything Connected
SPACE - S0 - 20210326 - Electric Earth Rotation Glitches Confirmed, Everything Connected
Good Morning, 0bservers!
Thursday, March 25, 2021
Is the nearest star cluster to the sun being destroyed?
Data from ESA's Gaia star mapping satellite have revealed tantalizing evidence that the nearest star cluster to the sun is being disrupted by the gravitational influence of a massive but unseen structure in our galaxy.
If true, this might provide evidence for a suspected population of 'dark matter sub-halos." These invisible clouds of particles are thought to be relics from the formation of the Milky Way, and are now spread across the galaxy, making up an invisible substructure that exerts a noticeable gravitational influence on anything that drifts too close.
ESA Research Fellow Tereza Jerabkova and colleagues from ESA and the European Southern Observatory made the discovery while studying the way a nearby star cluster is merging into the general background of stars in our galaxy. This discovery was based on Gaia's Early third Data Release (EDR3) and data from the second release.
The team chose the Hyades as their target because it is the nearest star cluster to the sun. It is located just over 153 light years away, and is easily visible to skywatchers in both northern and southern hemispheres as a conspicuous "V' shape of bright stars that marks the head of the bull in the constellation of Taurus. Beyond the easily visible bright stars, telescopes reveal a hundred or so fainter ones contained in a spherical region of space, roughly 60 light years across.
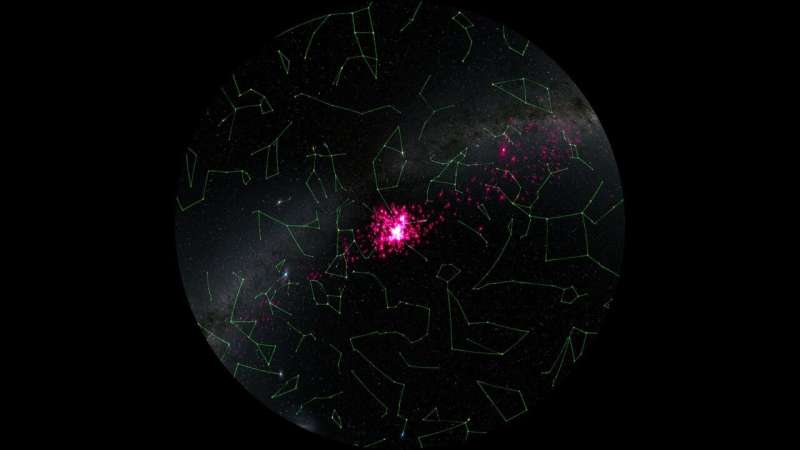
A star cluster will naturally lose stars because as those stars move within the cluster they tug at each other gravitationally. This constant tugging slightly changes the stars' velocities, moving some to the edges of the cluster. From there, the stars can be swept out by the gravitational pull of the galaxy, forming two long tails.
One tail trails the star cluster, the other pulls out ahead of it. They are known as tidal tails, and have been widely studied in colliding galaxies but no one had ever seen them from a nearby open star cluster, until very recently.
The key to detecting tidal tails is spotting which stars in the sky are moving in a similar way to the star cluster. Gaia makes this easy because it is precisely measuring the distance and movement of more than a billion stars in our galaxy. "These are the two most important quantities that we need to search for tidal tails from star clusters in the Milky Way," says Tereza.
Previous attempts by other teams had met with only limited success because the researchers had only looked for stars that closely matched the movement of the star cluster. This excluded members that left earlier in its 600–700 million year history and so are now traveling on different orbits.
To understand the range of orbits to look for, Tereza constructed a computer model that would simulate the various perturbations that escaping stars in the cluster might feel during their hundreds of millions of years in space. It was after running this code, and then comparing the simulations to the real data that the true extend of the Hyades tidal tails were revealed. Tereza and colleagues found thousands of former members in the Gaia data. These stars now stretch for thousands of light years across the galaxy in two enormous tidal tails.
But the real surprise was that the trailing tidal tail seemed to be missing stars. This indicates that something much more brutal is taking place than the star cluster gently 'dissolving."
Running the simulations again, Tereza showed that the data could be reproduced if that tail had collided with a cloud of matter containing about 10 million solar masses. "There must have been a close interaction with this really massive clump, and the Hyades just got smashed," she says.
But what could that clump be? There are no observations of a gas cloud or star cluster that massive nearby. If no visible structure is detected even in future targeted searches, Tereza suggests that object could be a dark matter sub-halo. These are naturally occurring clumps of dark matter that are thought to help shape the galaxy during its formation. This new work shows how Gaia is helping astronomers map out this invisible dark matter framework of the galaxy.
"With Gaia, the way we see the Milky Way has completely changed. And with these discoveries, we will be able to map the Milky Way's sub-structures much better than ever before," says Tereza. And having proved the technique with the Hyades, Tereza and colleagues are now extending the work by looking for tidal tails from other, more distant star clusters.
SPACE - S0 - 20210325 - CME & Solar Storm, California Quake Risk, SMOS
SPACE - S0 - 20210325 - CME & Solar Storm, California Quake Risk, SMOS
Good Morning, 0bservers!
Wednesday, March 24, 2021
Vast Fragments of an Alien World Could Be Buried Deep Within Earth Itself
They are among the largest and strangest of all structures on Earth: huge, mysterious blobs of dense rock lurking deep within the lowermost parts of our planet's mantle.
There are two of these gigantic masses – called the large low-shear-velocity provinces (LLSVPs) – with one buried under Africa, the other below the Pacific Ocean.
These anomalies are so massive, they in turn breed their own disturbances, such as the large phenomenon currently evolving within and weakening Earth's magnetic field, known as the South Atlantic Anomaly.
As for how and why the LLSVPs came to exist like this within the mantle, scientists have lots of ideas, but little in the way of hard proof.
What is known, however, is that these giant blobs have been around for a very long time, with many thinking they could have been a part of Earth since before the giant impact that birthed the Moon – ancient traces of the collision between Earth and the hypothetical planet Theia.
As for what happened to the rest of Theia, it's uncertain. Was it destroyed, or did it simply ricochet off into the eternity of space? We don't know.
Some researchers have suggested the cores of these two primordial planets may have fused into one, and that chemical exchanges wrought by this epic merger are what enabled life itself to thrive on the world that resulted.
Now, scientists have returned to these monumental questions with a new proposal, and it's an idea that reconciles the mysterious LLSVP blobs too, weaving them into the Earth/Theia hybrid hypothesis.
According to new modeling by researchers from Arizona State University (ASU), the LLSVPs may represent ancient fragments of Theia's iron-rich and highly dense mantle, which sank deep into Earth's own mantle when the two developing worlds came together, and has been buried there for billions of years.
"The Giant Impact hypothesis is one of the most examined models for the formation of Moon, but direct evidence indicating the existence of the impactor Theia remains elusive," the researchers, led by first author Qian Yuan, a PhD candidate studying mantle dynamics at ASU, explain in a summary of their findings presented last week at the Lunar and Planetary Science Conference.
"We demonstrate that Theia's mantle may be several percent intrinsically denser than Earth's mantle, which enables the Theia mantle materials to sink to the Earth's lowermost mantle and accumulate into thermochemical piles that may cause the seismically-observed LLSVPs."
While speculation has existed for years that the LLSVPs may be an alien souvenir implanted by Theia, the new research appears to be the most comprehensive formulation yet. The findings are currently under review, ahead of future publication in Geophysical Research Letters.
Beyond the mantle modeling, the results are also consistent with previous research suggesting that certain chemical signatures tied to the LLSVPs are at least as primitive as the Theia impact.
"Therefore, the primitive materials may [originate] from the LLSVPs, which is well explained if the LLSVPs preserve Theia mantle materials that are older than the Giant Impact," Yuan and his co-authors write.
We'll have to see how the rest of the scientific community respond to the team's findings, but for now at least, we've got another lead on just what these mysterious anomalies might be – and it's literally the most far-out explanation yet.
"This crazy idea is at least possible," Yuan told Science.
The findings were presented at the 52nd Lunar and Planetary Science Conference, conducted as a virtual event last week.


























